Cybersecurity
With the complexity of cyber-attacks continuing to evolve, our philosophical approach to cybersecurity solutions had to be reinvented. To adequately defend against such a vast array of cyber-attacks, it became clear that a robust defensive strategy had to be unified with an aggressive offensive strategy.
Successful network security cannot be accomplished by implementing isolated solutions. Instead, true network security is accomplished by integrating these individual solutions into a comprehensive mission to address the core weaknesses that are exploited in cyber-attacks.
These core weaknesses?
• Human Error
• Network Technologies
To address these common core weaknesses, DIS has assembled an arsenal of industry-leading technologies that seamlessly work together to defend your network integrity and take initiative on any future attempts to compromise your network.
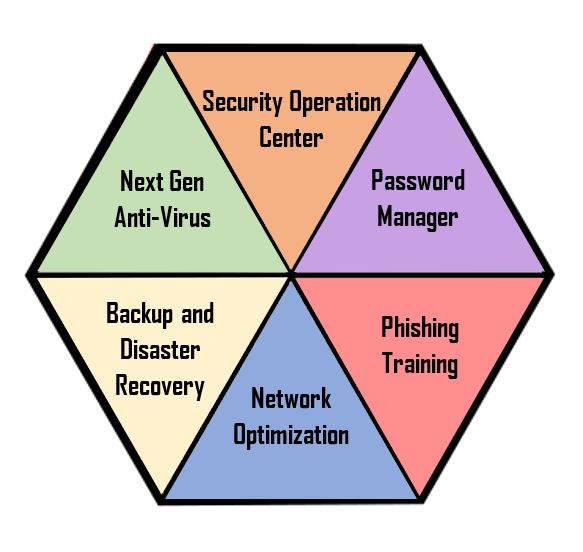
Next Gen Anti-Virus
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.

Security Operations Center (SOC)
Cybersecurity is heavily dependent on device management automation and machine learning. We’ve added a layer of human visibility to proactively identify potential threats.
Our U.S. based SOC is staffed with certified security engineers who personally inspect and analyze network traffic 24/7/365. Their sole mission is to serve as the eyes and ears on your network, identifying and responding to any system that has vulnerability.
Real time reporting and alerts allow us to remediate threats before they even arrive.
Password Manager
Security is frequently compromised from the simplicity of a login credential. Commonly used passwords often revolve around a dog’s name, a relative, or an important date. To boot, those same passwords are almost always used across multiple platforms.
Our Password Management solution securely stores military-grade passwords in a centralized, cloud-based platform that can be completely customized to the infrastructure of your business. The platform is mobile friendly and operates as a plug-in on all major web browsers, providing ease of use while increasing password complexity and differentiation.
Phishing Training
Phishing is one of the most common cybersecurity threats and continues to advance, becoming more sophisticated and difficult to spot. Our team of cybersecurity experts can provide your team with training on how to detect phishing attempts, safeguarding your valuable data from criminals.
Network Optimization
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.
Backup and Disaster Recovery
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.













